Call Us Now
+8615914489090

NFC (near filed communication) is a kind of "non-contact radio frequency identification" (RFID) and interconnection technology born out of wireless devices, and its application terminal is generally a mobile phone. NFC is an automatic identification technology that uses wireless radio frequency for non-contact two-way data communication to identify targets.
At present, NFC technology is mainly used for anti-counterfeiting and traceability. The anti-counterfeiting security is achieved through encryption and decryption algorithms of different security levels. In addition, NFC has also expanded many novel applications, such as the open detection function chip launched by Shanghai Fudan Microelectronics Group. , That is, the NFC chip itself can determine whether the tag is turned on. The general structure of this type of label is as follows:
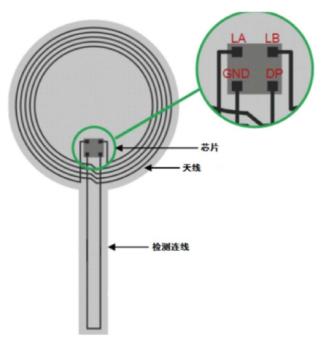
Obviously there is a long tail (the tail has various styles), this tail is the "detection connection" also called the tt line. When the item is opened, the tt line will be disconnected. When the NFC tag is read again, the tag can automatically identify whether Is it disconnected, is it "on". The conventional applications of this function are:
① Before opening: Consumers can easily obtain product anti-counterfeiting traceability information with a touch of a mobile phone.
② After opening: You can immediately participate in brand marketing activities such as points and lotteries to win rewards.
It can effectively enhance the interaction between the brand and consumers, help enhance influence and communication; it can carry out diversified marketing promotion, such as promotional activities, new product releases, product introductions, corporate information publicity, etc. The specific process is:
The first step: Consumers open the app or WeChat applet, use the mobile phone NFC to rely on a label to enter the authenticity verification interface. At the same time, the interface has the corporate brand promotion, product science introduction, marketing activity details, etc. designed by the brand owner. information. As shown in the right picture below, when the wine is not opened, the interface displays "the product is not opened". The content and style of this interface are designed by the brand according to their needs.

Step 2: Turn on the product, and the TT tail with the label that turns on the detection function will be cut off.

Step 3: Rely on the label in the mobile app or WeChat applet, and the label will automatically recognize "opened". And enter the interface with various precision marketing activities. as follows. As shown in the first picture, when the wine has been opened, the interface displays "the product has been opened", and then jump to the precision marketing page of the second picture, such as receiving red envelopes. The specific page content, style and marketing activities are all available. Design and develop according to demand to meet all marketing activities.

It can be seen that the label must be opened before entering the marketing activity interface, so that it can prevent being smashed in advance. For example, the common wool phenomenon in the previous QR code marketing system, that is, insiders will get the password and QR code information in advance, and then they can pick up the red envelope before the product is sold, or someone will quietly scrape away the item before buying it. Two-dimensional code password and take away the red envelope. And this kind of tailed NFC tag can be made into various styles, and can also be used on many products, such as gift boxes, cosmetic boxes, etc., on any product with an opening position.
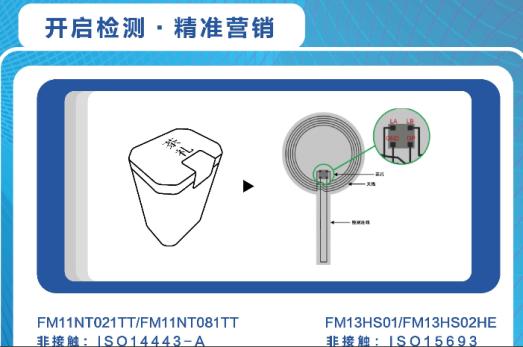
In addition, there is room for other applications to open the detection function, such as pour out real wine for fake wine, so the bottle must be opened, and after opening it can be detected by NFC that it has been opened, and it cannot be sold normally after changing the fake wine. Similarly, it is possible to prevent the transfer of "civet cats for princes".
The above is only a brief case description of the principle, this principle can have more application space.